Your first steps into cybersecurity
Get a demo
Loaker Tool Presentation
Cyber challenges of French SMEs

Serious consequences
Intrusion into computer systems presents major risks for business activity and sustainability.
Theft of sensitive data
Business interruption
Reputation damage
Regulatory non-compliance
Personalized Teaching
A personalized training path that transforms each simulation into tailor-made learning.
1. Email
Emails are custom-generated to best prepare each employee for a range of sophisticated attacks.
2. Scenario
Scenarios are adapted to each person's progress through Machine Learning.
3. Analysis
The employee's journey is analyzed to identify their missteps.
4. Personalized training
The employee watches a short training video adapted to their errors, progress, and scenario.
5. Validation
The employee completes a quick questionnaire to validate their training.
Cyclical Learning
Implement an iterative strategy for personalizing your campaigns to progressively prepare your employees for a wide range of threats.
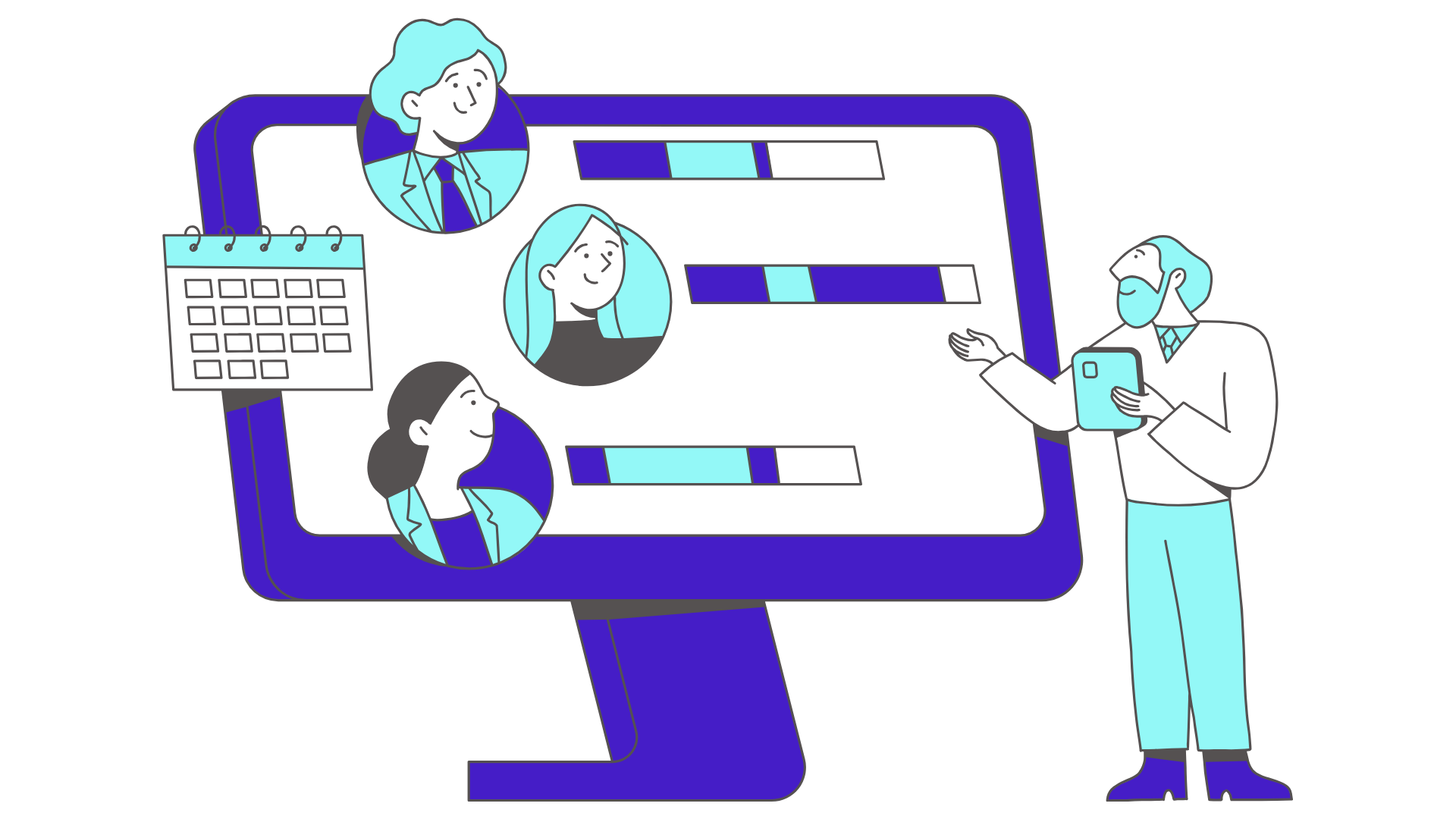
Campaign planning
Configure campaigns according to the metrics that matter to you and let AI optimize your employees' cyber awareness.
Recognized and impactful training
Gain useful cyber skills through a concise, cyclical teaching format that actively involves your employees. Training is adapted to each employee's progress and complies with ANSSI recommendations.
Real-time actionable monitoring
Simply analyze your campaign results through our dashboards and reports detailing your company's cyber maturity evolution.
Definition of concrete measures
Our data-driven approach allows you to implement a cyber strategy that truly meets your company's needs.
In-depth knowledge of your organization
This step allows the design of measures that are adapted and communicable to decision-makers.
- 📌 Real-time visualization of campaign results
- 📌 Employee training monitoring
- 📌 Analysis report on results and employee behavior
Implementation of solutions
Based on the analysis phase, tailor-made solutions are deployed.
- 📌 Study of relevant solutions
- 📌 Implementation of solutions
- 📌 Continuous monitoring of results evolution